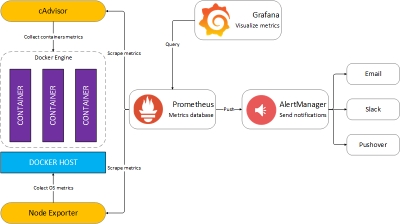
Installation is quite straightforward:
rm -fv csf.tgz wget http://www.configserver.com/free/csf.tgz tar -xzf csf.tgz cd csf sh install.sh
Next, test whether you have the required iptables modules:
perl /usr/local/csf/bin/csftest.pl
On a standard BHost VM running Debian or Ubuntu you will typically get an error message for the iptables IP v.6 module. If your VPS is hosted in London this does not matter at the moment. If you are based in Amsterdam install this package from the relevant repository .
Csf installation for cPanel and DirectAdmin is preconfigured to work on those servers with all the standard ports open.
Csf auto-configures your SSH port on installation where it's running on a non-standard port. It auto-whitelists your connected IP address where possible on installation.
You should ensure that kernel logging daemon (klogd) is enabled. Typically, VPS servers running RedHat/CentOS v5 have this disabled and you should check /etc/init.d/syslog and make sure that any klogd lines are not commented out. If you change the file, remember to restart syslog. See the csf.conf and readme.txt files for more information.
Webmin Module Installation/Upgrade
To install or upgrade the csf webmin module: Install csf as above Install the csf webmin module in: Webmin > Webmin Configuration > Webmin Modules > From local file > /usr/local/csf/csfwebmin.tgz > Install Module.
Important : Csf will NOT protect your system until you configure it correctly. By default it runs in training mode which will generate logs of incidents but will NOT block them
Configuration using Webmin
The csf congiguration is accessed via System > ConfigServer Security & Firewall
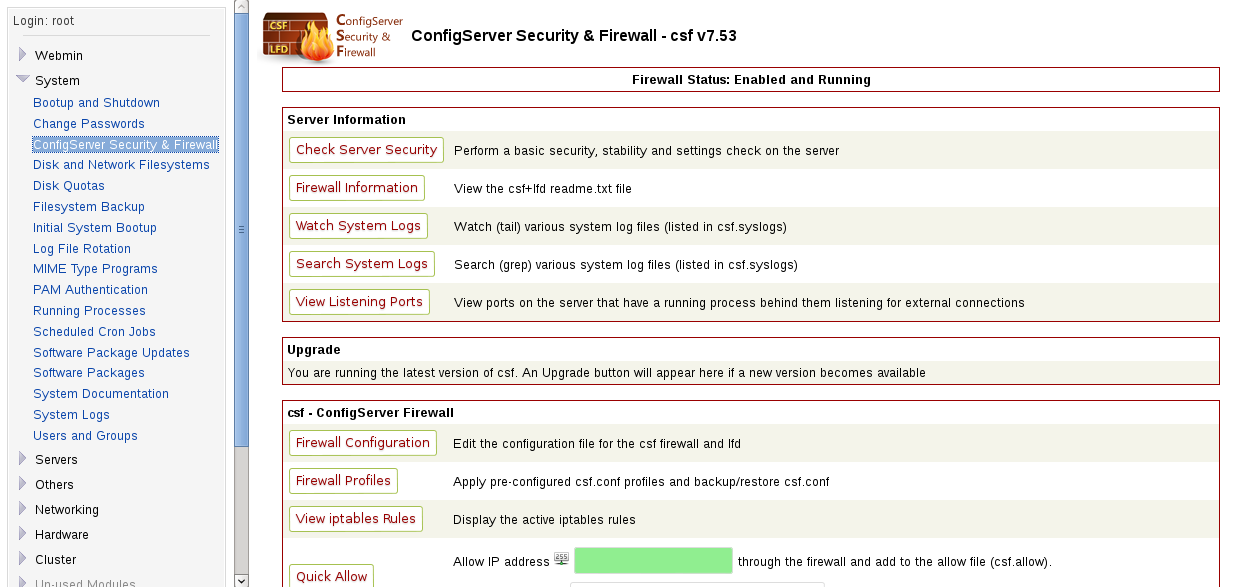
As you can see there are a huge array of configuration options. The most important one is Firewall configuration. This opens an even larger array of choices but do not be worried. Every choice is clearly explained in the configuration window.
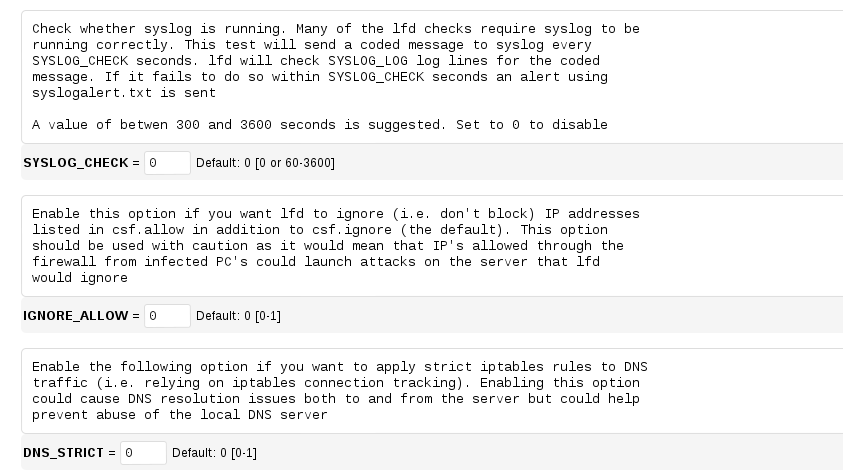
Most important is if you want to continue running in training mode for a while to tune your choices. My own preference is to switch this to zero i.e. operational immediately. If you are running services on unusual ports you may wish not to do this until you have opened the relevant ones.Some common ports that may cause problems at this stage are TCP 8080 for Tomcat and if you are running a VPN the TCP or UDP ports associated with that.
The top section of the configuration screen is for the firewall options, to open and close ports and logging options for incidents. You can block anything from a single IP address to whole countries. Do be aware that the tables used here each cause an extra lookup for your server and will slow it down. Country lookups are particularly slow.
The lower portion is to control the lfd (Login Failure Daemon). Personally this is the most important section to concentrate on. Your firewall will close ports that are not needed but you need to protect yourself on the ports you actually need open.
Brute force password attacks are easy to accomplish with a myriad of tools available, so even the most illiterate computer user can do this. Apart from using precious bandwidth and therefore slowing your site down for regular users, these pose a serious security threat. Any password attempts should be limited to three with a permanent IP block if that number is exceeded, for any service.
Using reputable spam blocking sites can also be enabled here. Be cautious using these as they also increase the table size your server uses for IP lookups and slow performance
I would not recommend process logging as it generates too many false positives.
Another tip, don't use the messaging services unless you really need them. Your mailbox will get flooded. It's surprising how many folks have nothing better to do than probe other systems looking for security flaws.
Reports
You should regularly check the repots that csf+lfd generate to ensure they are functioning as you wish i.e. not generating a lot of false positives and blocking regular visitors. Using Webmin a quick check of the tail of your logs can be viewed using System > ConfigServer Security & Firewall > Watch System Logs
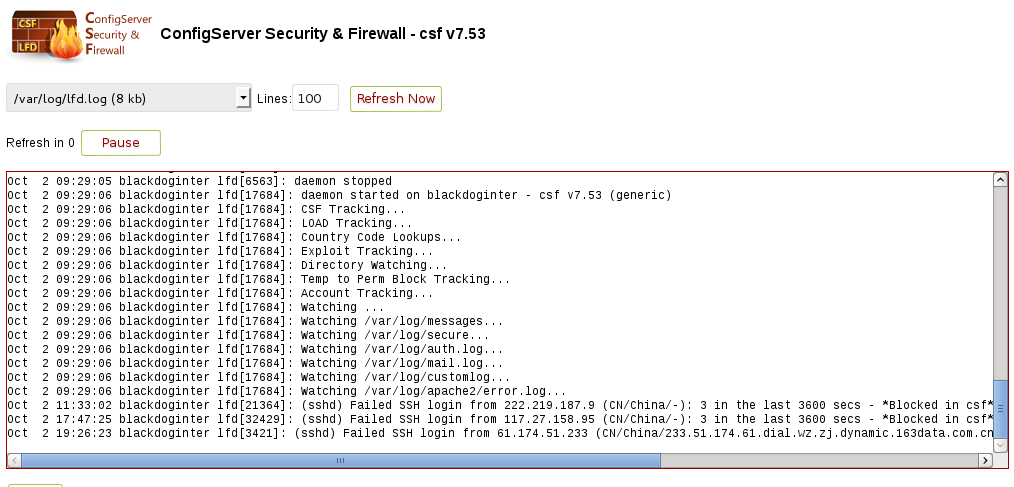
The full log address is shown at the top of this image.
Troubleshooting
If any service blocked from your VPS it is always worth checking if CSF is causing this. Use the Bhost terminal and stop the CSF daemon from running, then check the configuration in Webmin to ensure
1) You have the correct ports open for the service you are trying to run
2) Your IP address has not been blocked for excessive login failures. Make sure your WAN IP address is not in this table /etc/csf/csf.deny.
Conclusion
Csf +lfd work really well with their default settings.
You can easily personalise these to your own satisfaction.
If you would like help with any particular configuration options please do not hesitate to contact me via my website.